This lecture from purdue university talks about finite fields and their role in network security.
Finite fields in cryptography and network security.
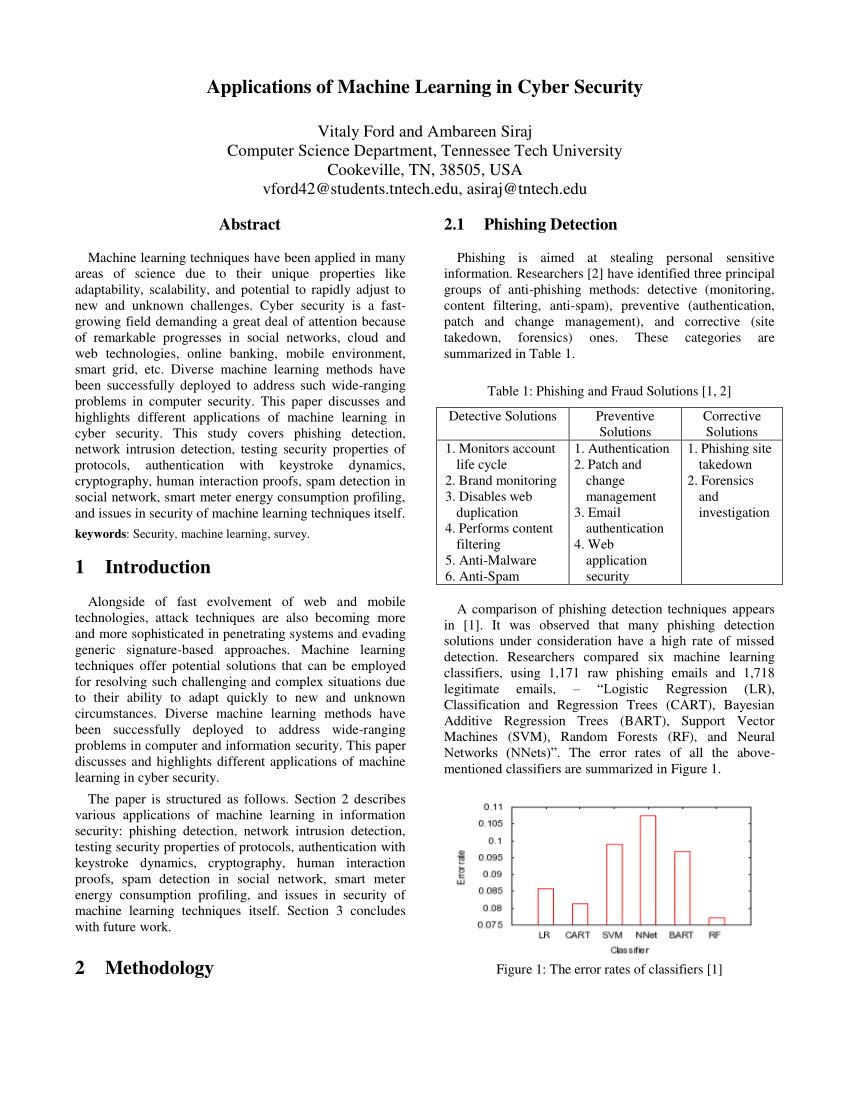
Groups rings fields modular arithmetic euclid s algorithm finite fields polynomial arithmetic prime numbers fermat s and euler s theorem.
Cryptography and network security chapter 4 fifth edition by william stallings lecture slides by lawrie brown chapter 4 basic concepts in number theory and finite fields the next morning at daybreak star flew indoors seemingly keen for a lesson.
A finite field is simply a field with a finite number of elements.
Finite fields of order p can be defined using arithmetic mod p.
However cryptography has not found a use for all kinds of finite fields.
I said tap eight.
Finite fields are important in several areas of cryptography.
It can be shown that the order of a finite field.
To review polynomial arithmetic polynomial arithmetic when the coefficients are.
Polynomial arithmetic theoretical underpinnings of modern cryptography lecture notes on computer and network security by avi kak kak purdue edu may7 2020 12 29noon c2020avinashkak purdueuniversity goals.
It is almost impossible to fully understand practically any facet of modern cryptography and several important aspects of general computer security if you do not know what is meant by a finite field.
Finite fields in cryptography.
Computer and network security by avi kak lecture4 back to toc 4 1 why study finite fields.
It can be shown that the order of a finite field number of elements in the field must be a power of a prime p n where n is a positive integer.
Finite fields part 3 part 3.
However finite fields play a crucial role in many cryptographic algorithms.
This means you can find finite fields of size 5 2 25 and 3 3 27 but you can never find a finite field of size 2 13 26 because it has two different prime factors.
Advanced encryption standard encryption.